RAW Cyber
Client
Industry
Fintech
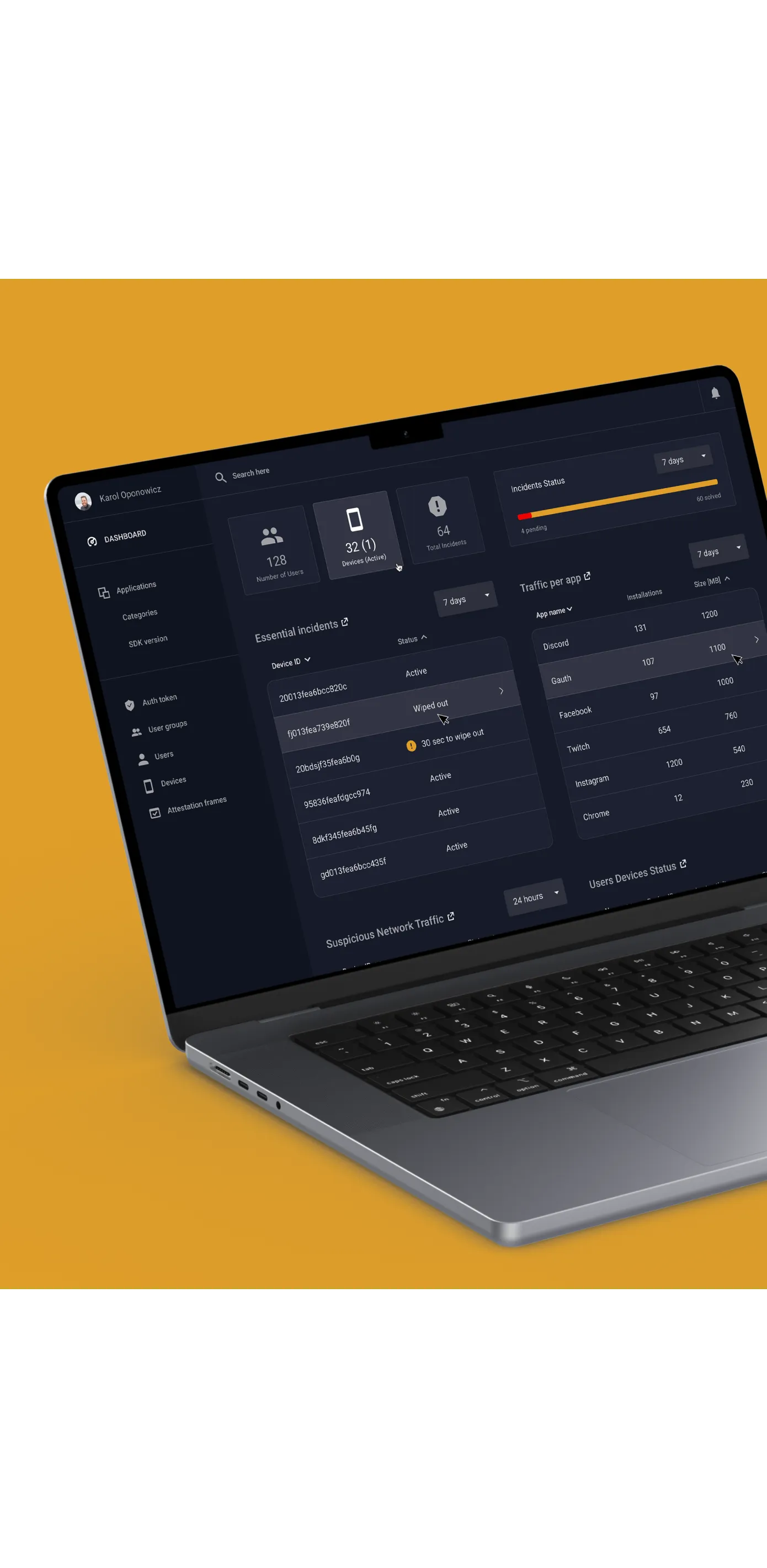
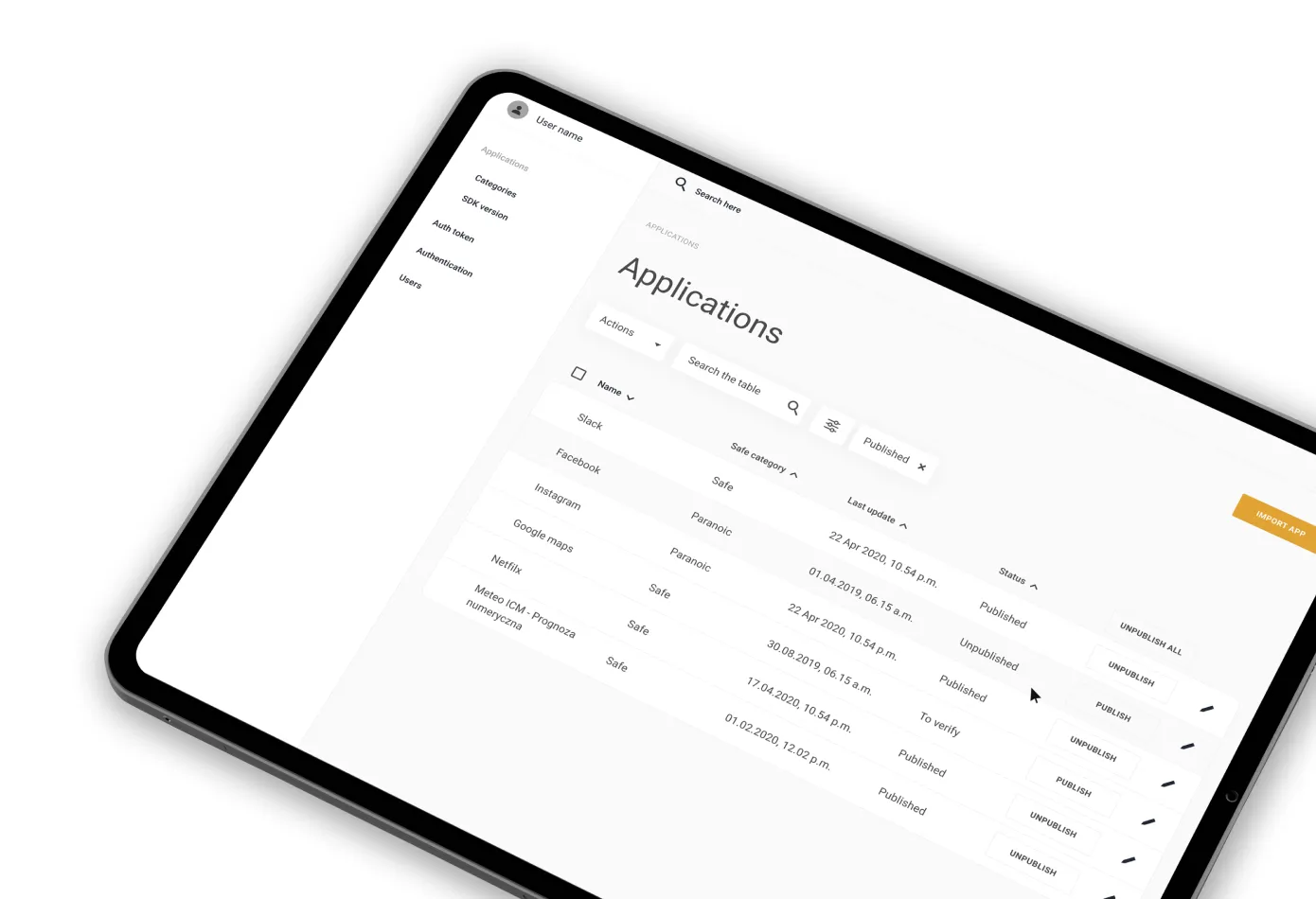
Secure Brand New Mobile Operating System

In order to discover what your product really needs
so far we worked with brands like:
Thank you for your message.